Warnings raised to take action to mitigate the Apache Log4j vulnerability – Log4Shell


Alerts have been issued by the National Cyber Security Centre (NCSC) as a detected vulnerability hits the open-source java logging library, Log4j, known as Log4Shell.
Log4j, developed by the Apache Foundation, is widely used in many applications and is present in many services as a dependency. This includes enterprise applications, including custom applications developed within an organisation, as well as numerous cloud services.
The vulnerability has been identified as CVE-2021-44228 and given the name Log4Shell. It can allow an attacker to execute arbitrary code by sending crafted log messages.
What action should you take to protect your data?
In order to ensure your data is fully protected, and prevent a vulnerability like this happening again, we would strongly recommend you invest in a reliable Web Application Firewall (WAF), such as HA WAF.
Log4Shell and other zero-day attack mitigations are quickly implemented into the HA WAF ensuring the right defences are in place.
Below is an example of how HA WAF would mitigate Log4Shell and other threats.

If you have applications connected with Log4j, the immediate action to take is migrate to the latest version of Log4j (currently Log4j 2.16.0). Version 1 of the Log4j library is no longer supported and is affected by multiple security vulnerabilities.
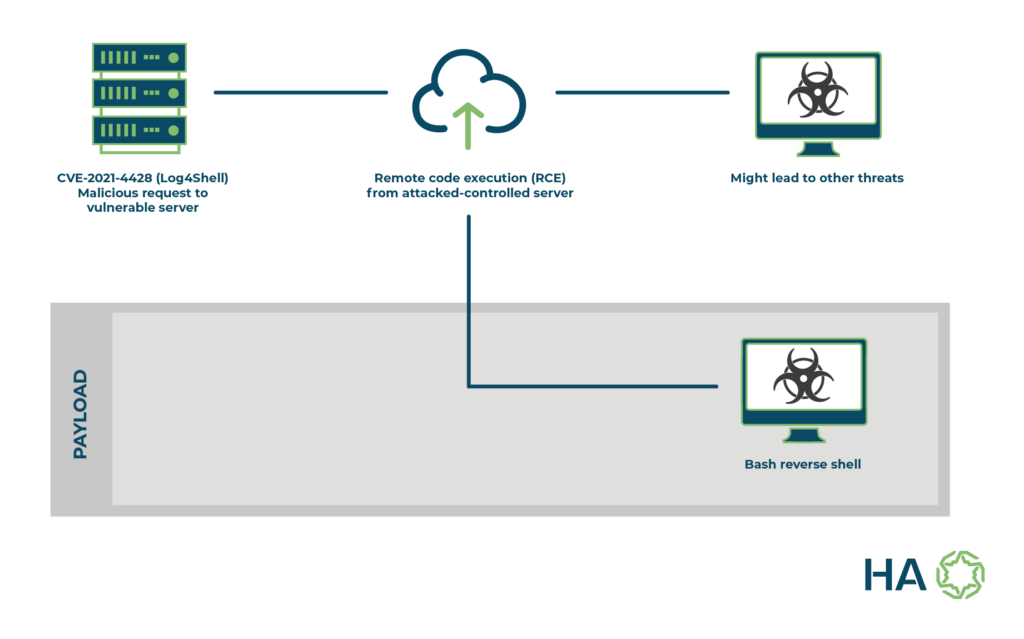
Below is an example of a possible infection chain from attacks which might exploit Log4Shell.
Get your data protected today:
Call 0800 8620844 or email us hello@weareha.co.uk
Visit www.weareha.co.uk/ha-waf for more information about HA WAF
To read more details about Log4Shell, visit the National Cyber Security Centre website