WordPress phishing attack CVE-2024-46188 Patch


Phishing attacks remain a constant threat in the ever-advancing landscape of cyber security.
The WordPress Security Team has issued an email alerting WordPress users about the latest critical vulnerability on users’ websites, urging them to install the “CVE-2024-46188 Patch” promptly.
The phishing email claims to be from the WordPress Security Team alerting users to a Remote Code Execution (RCE) vulnerability on their website, which is classified as a critical threat.
The email further advises users to download a plugin, allegedly a patch for the identified vulnerability, and install it on their site immediately.
However, masked as a plugin download, the “CVE-2024-46188 Patch” link provided leads to a malicious website.
Below is an example of what the deceptive email looks like:
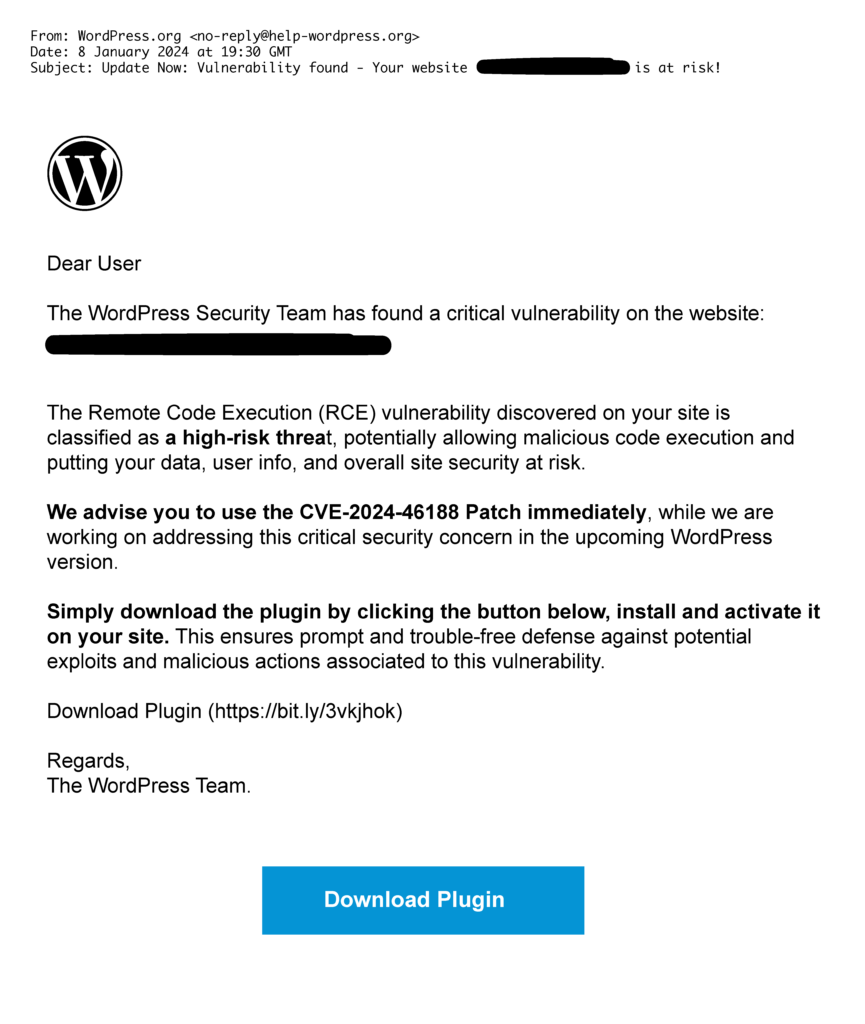
When it comes to identifying phishing scams, knowing what red flags to look for can help. In the case of CVE-2024-46188 Patch, here are some tips:
Legitimate organizations often address users by their names. Phishing emails may use generic salutations like “Dear user.”
Phishing emails often create a sense of urgency, instigating fear to prompt quick action. In this instance, the threat of a critical vulnerability and potential data compromise is employed.
Check the email sender’s address carefully. Phishing emails may use addresses that resemble legitimate ones but contain slight variations. ie donotreply@mailserver-wordpress.org
You’ll find this has been raised with the WordPress community forum, which can be found here: https://wordpress.com/forums/